Log4shell – the newest vulnerability
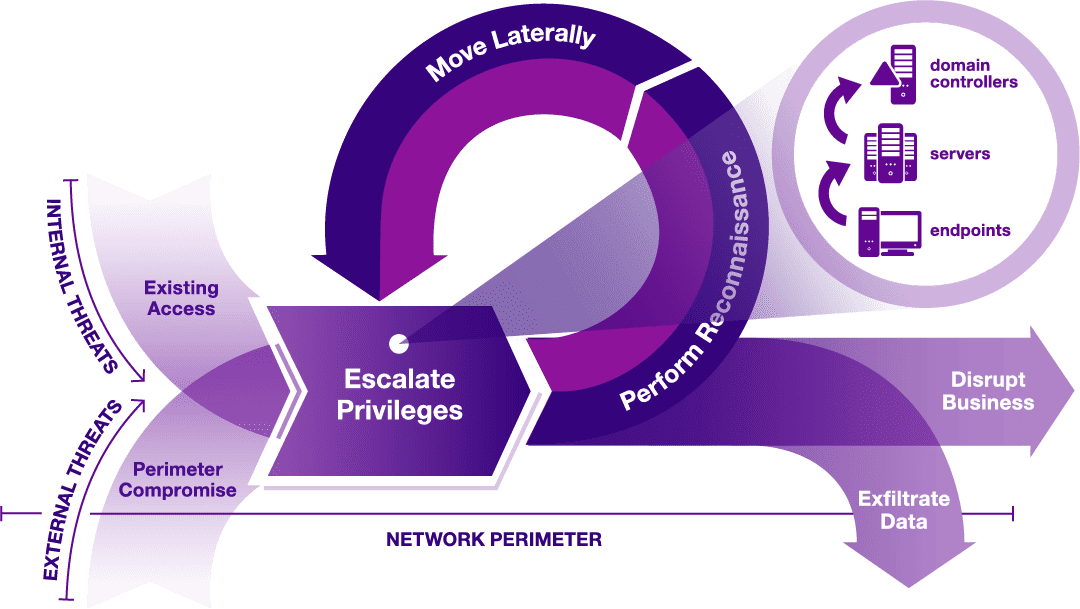
Introduction On Thursday, December 9th, the vulnerability CVE-2021-44228 known as “Log4shell” was made public, sending large companies such as Twitter, Amazon, Google, Cloudflare, and many others in a rush to patch it before any damage could be done. Not only are large companies affected, but many applications and servers utilizing [...]