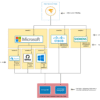
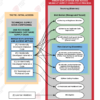
How MDR Secures Your Organization
Obscurity Labs understands the complexities of organizational security operations and therefore provide our security services as a collaborative process. We work closely with our customers to establish a strong foundation that enables us to mature their Security Operations Program. Our team of talented security engineers and analysts provide white-glove managed security services that are customized to fit the unique needs of each of our customers. Our customers build strong relationships with our team members and know exactly who to call for support during an issue or security incident. Obscurity Labs collaborates closely with our customer’s IT and security teams to resolve incidents and mature the organization’s overall security posture. By working closely with our customers and aligning our goals, we’re able to effectively lower MTTD & MTTR over time. We also offer on-tap security consulting in the form of senior leaders, IT, and security personnel capable of supporting our client’s team at any level whenever needed.